Turnstiles from a hacker perspective - Part 1
Attacking face recognition, lock bumping and physical security design issue
Disclaimer
This Security Advisory is provided on an "as is" basis and do not imply any kind of guarantee or warranty. Your use of the information in this publication or linked materials is at your own risk. PRIDE Security reserves the right to change or update this content without notice at any time.
Introduction
Welcome, information security enthusiasts!
Before we begin exploring the topics of this chapter, we would like to invite you to check out a video version of the same content. In the video, we visually address the key points and provide a dynamic experience. If you prefer to learn in a different way, click play below.
Now, if you're ready to follow along with this chapter in writing, keep scrolling down the page. Let's go!
Today, we will be diving into an exciting and often overlooked topic in information security blogs and videos: offensive security with a focus on turnstiles used in physical access control systems. Throughout this series, we plan to share project details and provide insights from internal 'Proud to be PRIDE' presentations.
In this chapter, we will dedicate the next few minutes to an immersion in facial recognition aspects and the physical security of turnstiles. In the upcoming chapters, we will cover topics such as the use of implants for replay attacks, access to the logical network through turnstiles, and attacks on turnstile management software.
Facial recognition and physical security at turnstiles
Turnstiles are located in various places, ranging from corporate buildings to subway stations. Access is often controlled through methods such as cards, badges, facial biometrics, fingerprints, among others. Turnstiles play a crucial role in physical security, determining who is allowed to enter a specific location.
In the context of physical penetration testing, turnstiles play a crucial role in controlling access. The idea of physical penetration testing is to assess how easy or difficult it is for an unauthorized individual to gain access to the facilities. To achieve this, various techniques are used to determine the physical vulnerabilities in the environment and how they can be exploited.
In summary, the goal is for the attacker to gain unauthorized access within the company being tested. Once inside, the goal is to expand access to the logical network. This may involve deploying implants, infecting computers, extracting confidential information, and so forth.
Access controls for Wolpac turnstiles
Let's delve into the details of a test conducted by PRIDE Security involving Wolpac’s turnstiles. These turnstiles are commonly used in corporate environments, and the client aimed to modernize the company's access control system during the COVID-19 pandemic.
The upgrade included a module from ZKTeco, introducing facial recognition features that could operate even when the user was wearing a mask. Additionally, the system had the capability to measure a person's temperature. With this enhanced system, employees could gain access after facial recognition, provided their temperature was within the appropriate limits.

It's important to highlight that the vulnerabilities we explored are not specific to this turnstile and therefore can also be applied to many other access control systems used in residential and commercial buildings.
When analyzing this type of access control mechanism, there are two approaches to user authentication. The first is local authentication, suitable for smaller environments, such as small residential buildings, where only residents have access permission, and all information is contained within the recognition module itself. In a corporate context, the most common practice is information centralization. In this scenario, various devices, such as badge readers, biometrics, and others, are employed, with all data being transmitted and managed centrally.
In this analysis, we will explore aspects related to security, starting with physical security, then moving on to the authentication mechanisms and protocols in use, and finally, we will investigate vulnerabilities in the management software. As mentioned earlier, it is a common practice in the corporate environment to centralize this information and manage it through specific software.
Let's begin by examining the facial recognition mechanism used.
Facial recognition evasion
Before delving further, it's pertinent to emphasize that the client had communicated that the supplier had conducted numerous tests on this device to ensure the presence of robust security mechanisms, aimed at preventing attacks such as the reuse of photos, videos, and other potential vectors. In light of this assertion, one of our primary objectives was to scrutinize the efficacy of these mechanisms.
We initiated the process by monitoring employee entries and exits at the company. Our aim was to capture a series of photographs of various employees, varying distances and angles, without, of course, attracting their attention. The intention was to use these photographs in the turnstile evasion process.
While capturing these images, several key considerations were taken into account:
- The need for high-resolution photos, as the influence of resolution on facial biometric identification was unknown.
- Conducting tests with various types of paper to identify the most suitable for this approach.
- Ensuring that the prints are life-size, reflecting the person's head size closely to reality.
In this context, we present the captured image of an employee who will serve as an example. It can be noted that we added a facial mask to the printed face of the employee.

As mentioned earlier, the turnstile allows recognition of the employee even while wearing a mask. We used suitable paper and printed in high quality. The key to deceiving the system is, to identify the appropriate angle and position the photo correctly, allowing the turnstile to read it, and, as a result, grant access. As demonstrated, access was granted.
Figure 3 - Opening the turnstile using a printed photo with a mask placed over it.
In this type of attack, three factors are crucial. In addition to considerations related to the quality of the photo and printing on appropriate paper, there was a very important aspect, the positioning. It was essential to position the paper at an appropriate angle to ensure recognition by the turnstile. Otherwise, we could have tried for a long time without any success. Distance and angle were very important.
Complementary assessments
Another important point involved temperature reading. As mentioned, this turnstile could measure temperature. For example, if facial recognition was successful but the user had a fever, their access could be denied, or their manager could be informed. Therefore, in addition to ensuring the correct distance, and proper angle, another factor was to ensure that the turnstile could measure the temperature of the attacker adequately, thus allowing access.
Finally, a relevant point was related to the algorithm's vulnerability when using a mask. As observed, we placed a real mask in front of the person's photo in the video, which significantly facilitated the authentication process. Without the mask, recognition algorithm became considerably more robust. However, when using the mask, there were fewer facial reference points, allowing evasion.
Facial recognition evasion using a social media photo
Additionally, we explored a variation of this attack, where we used photos found on social networks. This means that an attacker does not need to monitor the entry and exit of employees, avoiding unnecessary exposure in certain situations.
Our initial strategy focused on identifying employees through LinkedIn, specifically those associated with the company. The figure below, extracted from the PRIDE Security profile, illustrates how the search for employees can be straightforward.
Therefore, in a similar manner, we tracked the client's employees and then searched for their accounts on other social media platforms, such as Facebook and Instagram.
After identifying an employee whose image had suitable angles and quality, we proceeded to print that photo in high resolution using high-quality paper. The printing process followed methods similar to those employed in the previously described attack.
It's important to highlight that, as part of the experiment, we applied paint to the mouth region in the photograph to simulate the use of a facial mask. Interestingly, the "mask" was created using an ordinary pen commonly used in daily life.

To our surprise, the facial recognition system was able to identify the person in the image despite the alteration made. It's important to note that other factors, such as temperature analysis, were also taken into consideration.
Just out of curiosity, we positioned the photo at an angle where the camera read the face while the sensor, located above on the turnstile, was able to read the attacker's forehead's temperature instead of the paper.
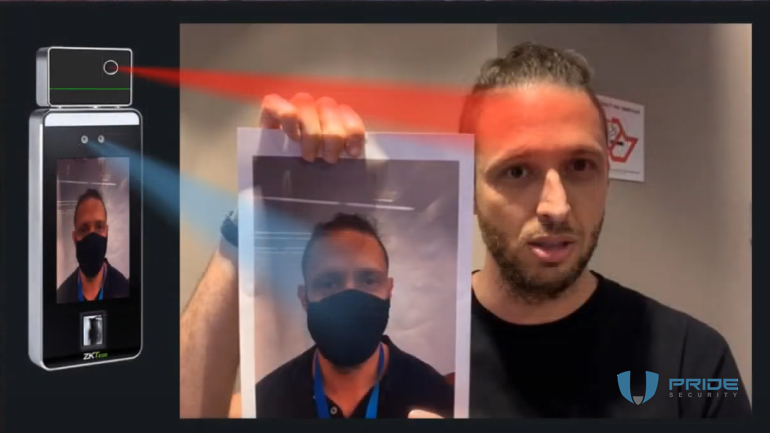
In this way, we were able to demonstrate that the facial recognition algorithm, is not robust, especially when people wear masks or use photos with painted masks.
Our aim is only to illustrate and explain the attack; in real cases, the attack can be carried out more discreetly. For example, why not print out the person's photo and stick it in a book that you carry in your arms? Why not print the person's photo on the T-shirt you are wearing? The possibilities are limitless.
Figure 7 - Photo of a PRIDE Security consultant hidden in a book and printed on a t-shirt
Can you carry out one of these attacks discreetly in real life? Send a video to PRIDE Security demonstrating your successful attack discreetly and win an exclusive PRIDE’s T-shirt and be part of our next video. Yes, we will put your video in the next edition, if you agree! And of course, you must have authorization to carry out the attack, we won't take cigarette packets to anyone who gets arrested! 😄

Access to wiring and internal components of the turnstile
So far, we've discussed attacks on facial recognition mechanisms. However, when examining the turnstile shown in the videos, we noticed that there is a badge reader's device. Usually, this badge reader module is attached with glue, and its removal is simple.

Once it is removed, we gain access to the wiring and various components inside the turnstile that may be of interest to an attacker. For example, this could allow the insertion of an implant, which in this case would be difficult to detect since it is not externally exposed.
When we address the issue of unauthorized external access to the card reader's module, we enter the realm of physical security. It's worth noting that the turnstile is fitted with a lock to restrict access to its internal parts. Therefore, in addition to controlling access to specific areas within the company, the turnstile also has its own layer of physical security. This is an area of concern because a failure in this mechanism could permit a series of attacks.
Let's analyze how we can attack this layer of security that restricts access to the internal area of the turnstile.
Use of a bump key for unauthorized opening
One of the methods we used to open this turnstile without authorization is known as 'bump attack' or 'lock bumping'. This type of attack is quite effective on a wide range of locks that use pins. We used keys called 'bump keys' for this type of attack. Here are some examples of 'bump keys.'

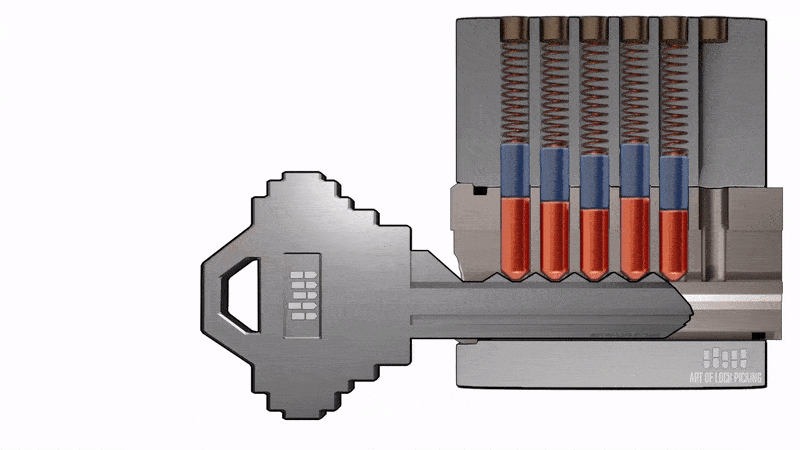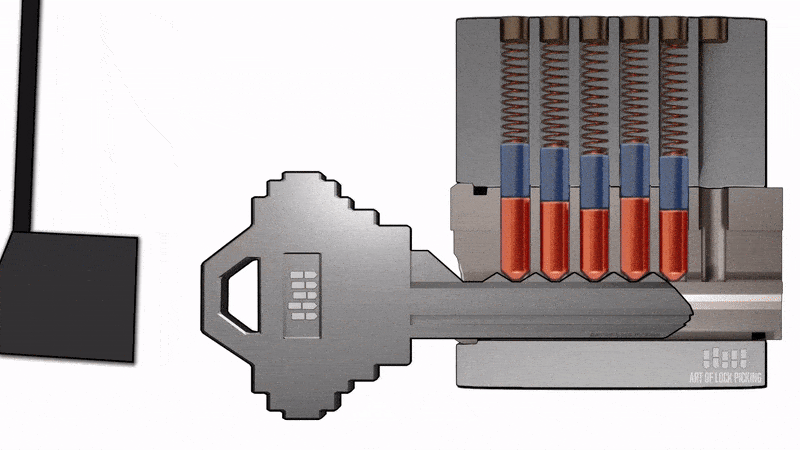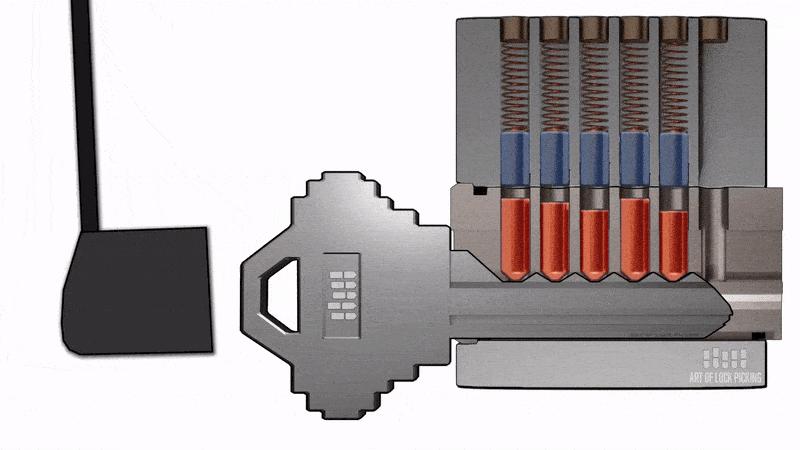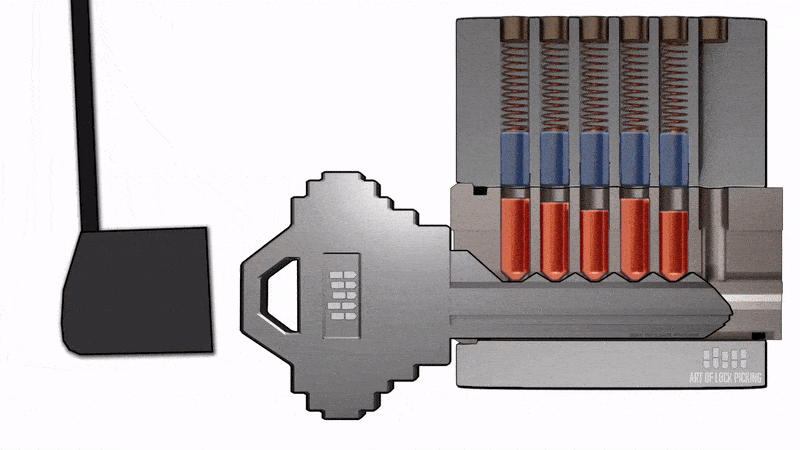
When we take the correct key for the lock, we can see that they have teeth. These teeth, when inserted into the cylinder, align the pins, as shown in the animation.
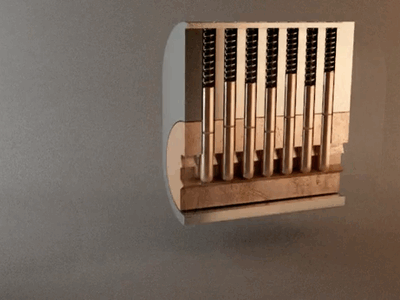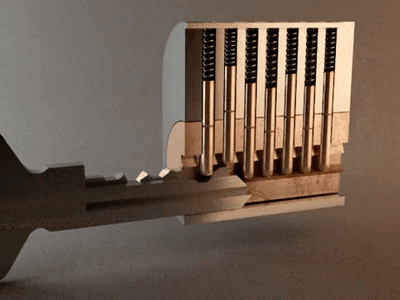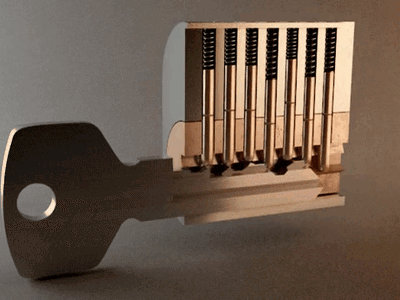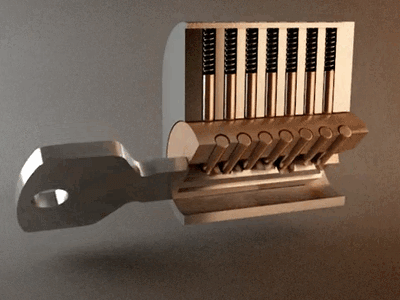
When the teeth have the correct size, the key goes into the lock, and then the pins are moved in the right position, allowing us to rotate the cylinder, for example, opening or closing the lock.
The 'bump key' is nothing more than a key following the same standard as the lock we are attacking. The difference is that it has cuts at the minimum level allowed by the standard, meaning it has teeth at the lowest allowable height.
The distance between the teeth is maintained according to the standard. The principle of the 'bump key' is that it goes into the lock but does not correctly align the pins due to the teeth being at the minimum height. In other words, these teeth are shorter and do not create the necessary contact to align the lock's pins correctly.
However, when we strike the key, this impact causes the pins to move, and for a fraction of a second, they may align within the cylinder, allowing for the unauthorized opening of the lock.
Now let's observe the attack in practice. We are using a small hammer to create the impact on the bump key inserted into the turnstile lock.
Figure 12 - Unlocking the turnstile using a lock bumping attack.
The process of opening the lock with the 'bump key' is very fast. These attacks are very interesting and swift. However, they are somewhat noisy, which, depending on the environment, can attract unwanted attention and this makes the option unfeasible in some, if not most, cases.
So, we might wonder how one can open the same lock without making a noise? We have observed a security design problem in this turnstile. Let's analyze this problem in detail.
Design issues in the turnstile
On the turnstile door, there is a kind of latch that is fastened by a hook, which is located on the inside of the turnstile. When we insert the appropriate key and turn the cylinder, it moves an iron bar responsible for shifting the hook that locks the door, either up or down, allowing the door to be closed or opened.
Figure 13 - Operation of the locking mechanism on the turnstile
We can see that this lever that locks the mechanism is located exactly on the door's junction, presenting a small opening that provides access to this lever when the door is closed.
By inserting a thin, solid object, it is possible to manipulate this lever and open the door in an unauthorized manner, extremely quickly and quietly, as demonstrated below.
Figure 14 - Alternative method of opening the turnstile
Conclusion
In this chapter, we conducted an analysis of vulnerabilities associated with facial biometrics systems, highlighting how attackers can exploit these loopholes to gain unauthorized access to environments protected by turnstiles. Additionally, we examined the physical security measures inherent in turnstiles and identified design flaws and lock-picking techniques that amplify the vulnerability of these systems.
This analysis not only exposes the weaknesses present in current access control systems but also emphasizes the ongoing need for improvement and innovation in both physical and digital security.
Our journey to understand and enhance turnstile security is an ongoing process. In the next chapter of this series, we will delve deeper into our understanding of security implants and replay attacks, expanding our knowledge of challenges and solutions in contemporary security.
The journey into turnstile security continues! Stay tuned!
Acknowledgements
| Name |
|---|
| Cleriston Freitas |
| Felipe Sanches |
| Ricardo B. Gonçales |
| Wendel G. Henrique |
About PRIDE Security
PRIDE Security is a company specialized in information security that focuses on technical excellence and personalized services. Founded by information security experts, we have worked in various types of projects, from ATM (automated teller machines) penetration testing to national security projects.
Composed of an experienced team of more than 15 years in the market and with technical excellence proven by national and international technical recognition, PRIDE Security sees in each project a new challenge to deliver more than expected.
As proof of international technical recognition, our professionals are constantly approved or invited to lecture on security events around the world. We cite below some examples of congresses, conferences and seminars focused on information security, which we participate as lecturers or coordinators of the technical groups:
- Blackhat – USA
- RSA Conference – USA
- Defcon – USA
- ToorCon – USA
- Blackhat – Europe edition
- OWASP AppSec Research – Europe edition
- OWASP AppSecEU09 – Europe edition
- Troppers – Germany
- H2HC (Hackers 2 Hackers Conference) – Brazil
- YSTS (You Sh0t The Sheriff) – Brazil
In addition to lecturing at major security events around the world, our team of experts are also responsible for writing various papers, co-author of offensive technology patent registered in the United States of America (US8756697), finding and publishing security vulnerabilities in famous software such as Sun Solaris, FreeBSD / NetBSD kernel, QNX RTOS, Microsoft ISA Server, Microsoft Word, Adobe Flash, Adobe PDF, among others.
Many organizations of all sizes concerned with information security rely on PRIDE Security. If you desire, we will be pleased to connect you with our customers to share about their experience with our services.


