Horacius (IAM) - Local privilege escalation, even without a Windows account.
Unauthenticated privilege escalation in Horacius (Identity and Access Management) - CVE-2024-29417: a security software vulnerability allows for local privilege escalation, even when Windows is locked.
Disclaimer
This Security Advisory is provided on an "as is" basis and do not imply any kind of guarantee or warranty. Your use of the information in this publication or linked materials is at your own risk. PRIDE Security reserves the right to change or update this content without notice at any time.
Introduction
Welcome, information security enthusiasts!
Before we dive into the content of this blog post, we'd like to invite you to check out the video version of the same content for a more engaging experience. In the video, we visually address the key points and provide a dynamic presentation. If you prefer to learn through a different medium, click the play button below.
This vulnerability was uncovered by PRIDE Security in two closely spaced tests. The first was a physical penetration test that encompassed the internal environment, while the second was a security evaluation of a laptop sent by a client. These simultaneous tests led to the identification of CVE-2024-29417 in an E-TRUST Identity and Access Management (IAM) system.
About manufacturer
"With a mission to protect its clients’ information assets for over 20 years, E-TRUST is a leader in information security in Brazil and Latin America and is part of the Objective Group, the holding company dedicated to investments in the information technology sector.
With proven and pioneering expertise in Information Governance and Security, E-TRUST is the only company in the industry with all its processes in compliance with the ISO 27001 standard. Cited in Gartner’s Identity Management Magic Quadrant from 2011 to 2016, has a renowned portfolio of Managed Security Services, Projects and Information Security consultancy with operations in more than 10 countries, including projects in the United States, Mexico, Argentina, Uruguay, Chile, Spain and others.
Its clients are listed on the IBOVESPA, NY Stock Exchange, Fortune 100, 500 and Fortune Global 500."
Site: https://www.e-trustsecurity.com/
About the product
"Information security and proper identity management is key to having a secure workplace for any organization.
Horacius is a comprehensive IAM system providing state of the art features like HR systems integration, segregation of duties, incident management, IAM security event correlation and an integrated incident management workflow."
Site: https://www.e-trustsecurity.com/horacius-identity-governance/
Affected version
1.0
1.1
1.2
The manufacturer has reported that the vulnerability was fixed in version 1.3. However, it is important to emphasize that PRIDE Security has not validated this fix.
Summary
The PRIDE Security team has identified a critical vulnerability in the Horacius software, developed by E-TRUST. This vulnerability poses a significant threat to system security, as it allows attackers with physical access to the device, without the need for access credentials, to gain full control over the Windows operating system.
A security issue was identified in the Horacius software’s feature that implements a button “Esqueci / Bloqueei a SENHA" (or "Forgot / Locked the PASSWORD") on the Windows logon screen, even when no users are logged in.
The PRIDE Security team was able to exploit this feature to escalate privileges on the system, reaching the NT AUTHORITY\SYSTEM, which grants privileged access to an attacker.
With this level of access, an attacker could perform a range of malicious actions, including disabling monitoring and security software, installing malicious programs, and stealing sensitive information stored on the device. The vulnerability therefore opens the door to sophisticated attacks.
CVE-2024-29417: Horacius - Unauthenticated Privilege Escalation
A user with access to the Windows logon screen can escalate privileges to NT AUTHORITY\System by first disconnecting the device from the network and then clicking on the button created by Horacius. This sequence is essential for successful exploitation and requires local access to the computer. Once the network is disconnected and the feature activated, a web browser opens under these specific circumstances. This grants the attacker several options, such as engaging printing functions or saving the current web page. Utilizing these features, an attacker can ultimately access a privileged command prompt, including tools like cmd or PowerShell.
Steps to Reproduce
On the login screen, disconnect from the network by simply putting the system in airplane mode, then select “Esqueci / Bloqueei a SENHA” (or "Forgot / Locked the PASSWORD").
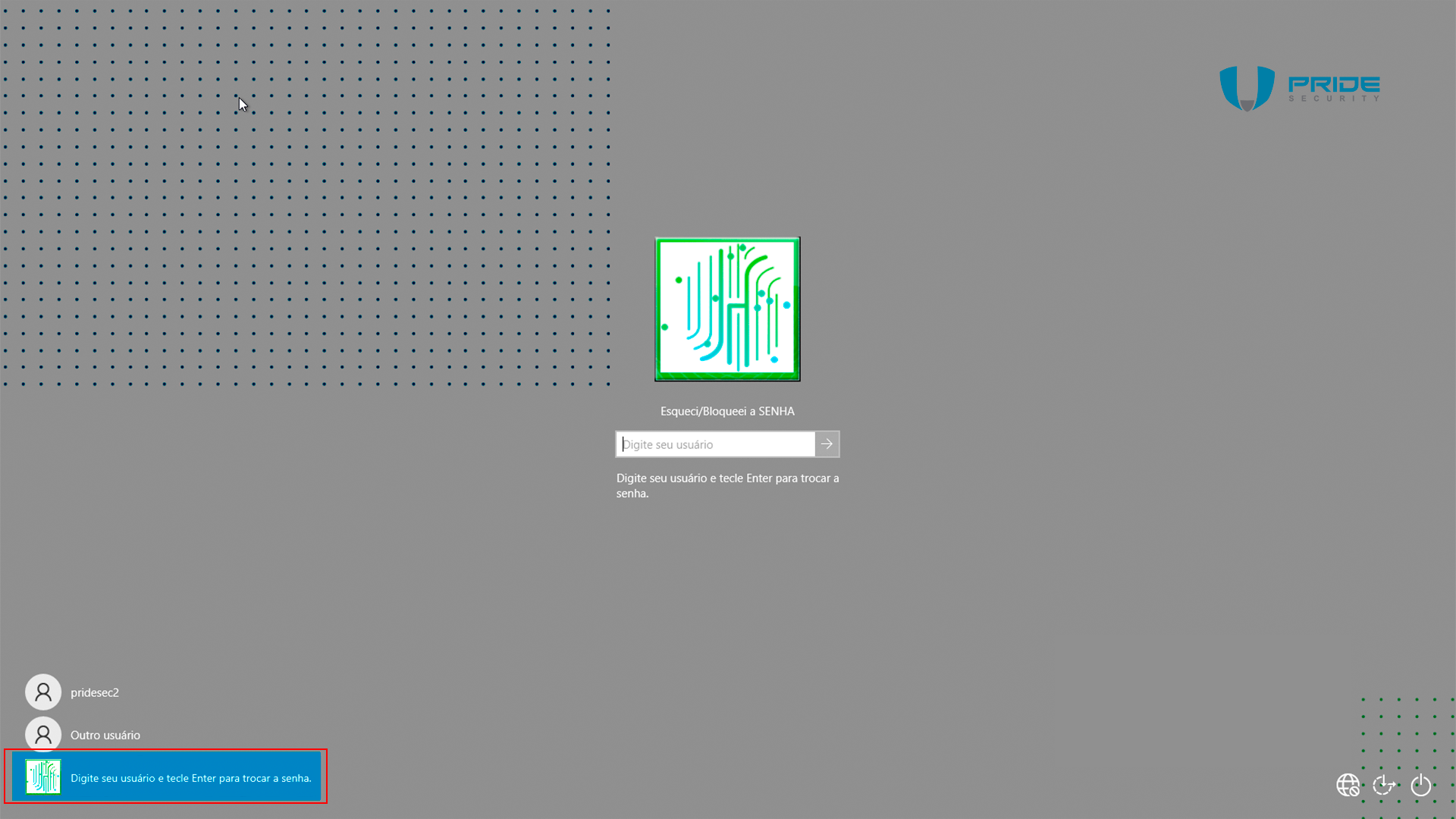
When this option is selected on a computer that is not connected to a network, any user can be entered; during testing, the 'admin' user was specified.
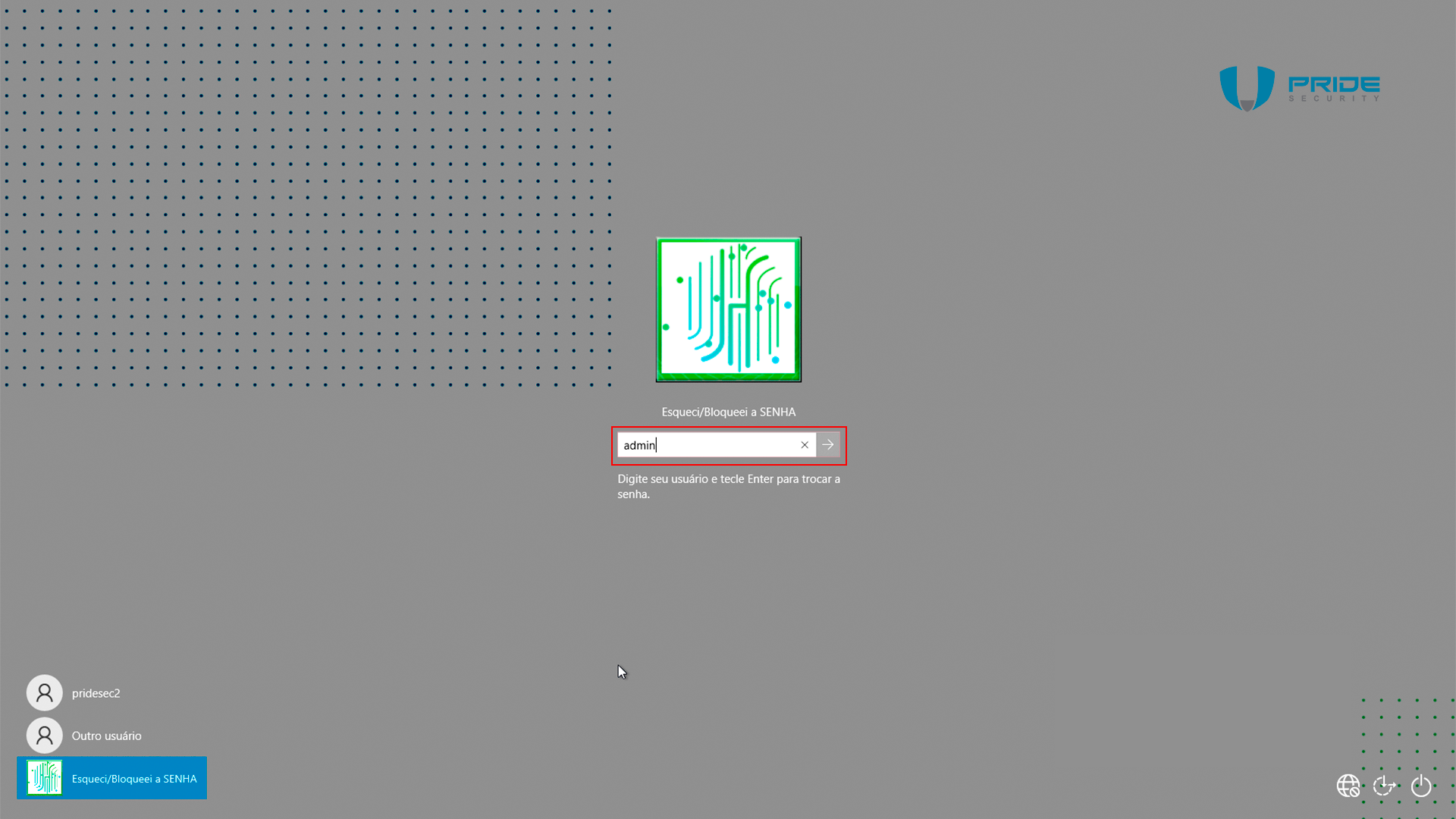
A web browser will appear, it will be unable to connect to the Horacius server and will therefore display an error message. Click on the sole link visible on the screen, “Atualizar a página” (or “Refresh the page”).
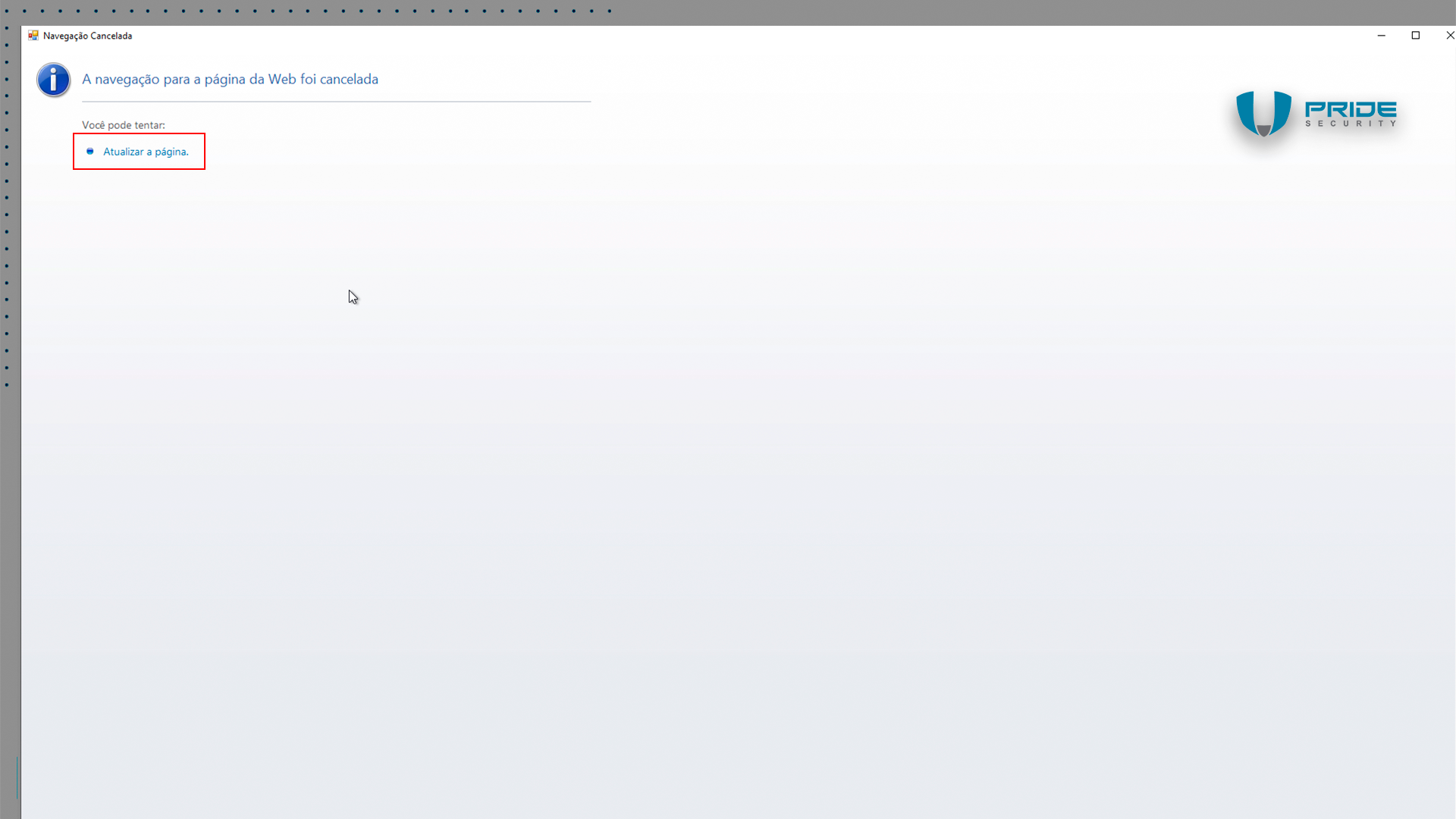
When clicking on the option “Atualizar a página” (or “Refresh the page”) with the device disconnected from the network, another error screen is presented.
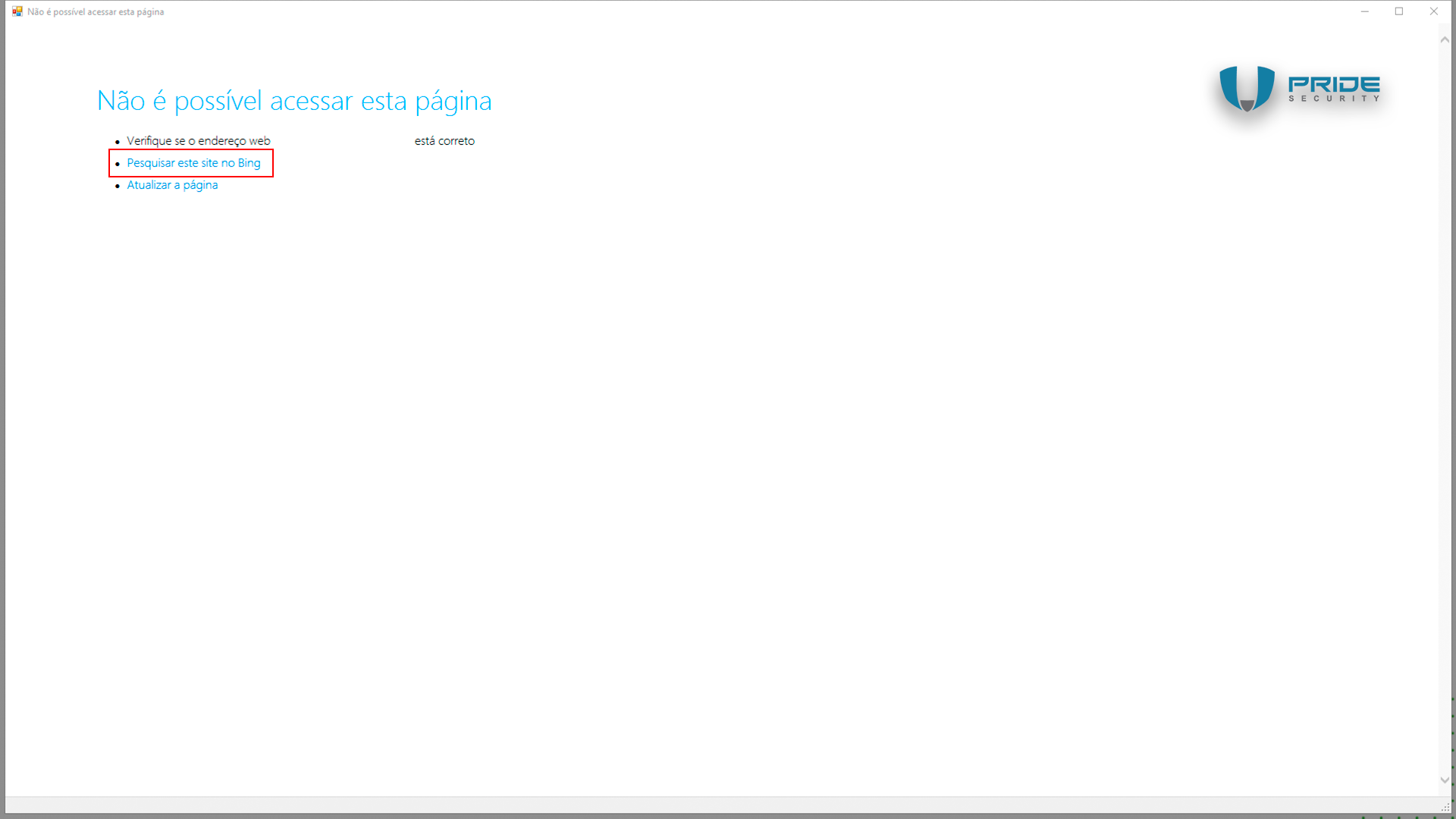
When you click on the option "Pesquisar este site no Bing" (or "Search this site on Bing") while holding down the SHIFT key, Internet Explorer will load on the screen, as shown below.
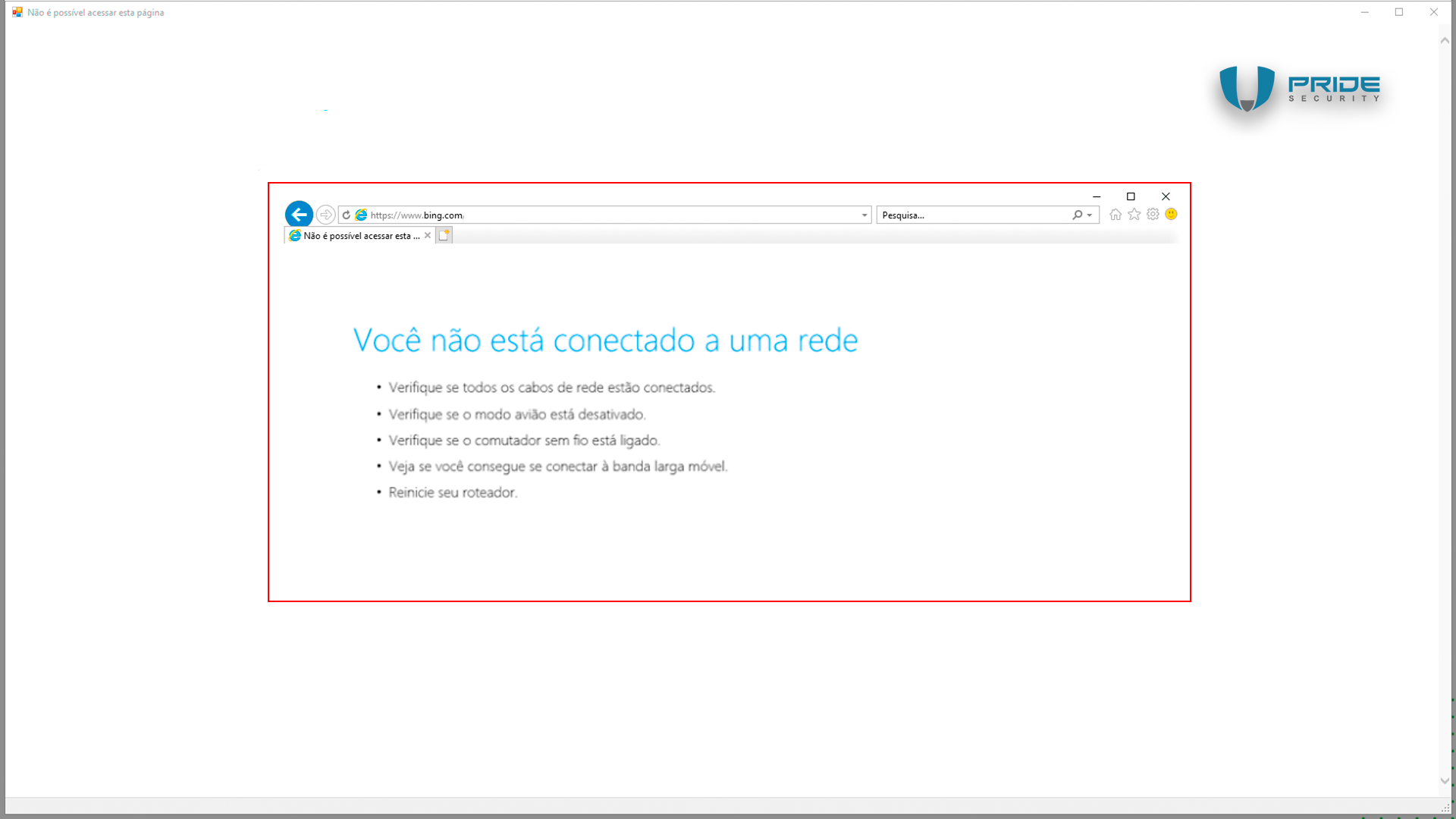
With Internet Explorer open in the foreground, the attacker can simply press the CTRL + S keys simultaneously to save the displayed error page.
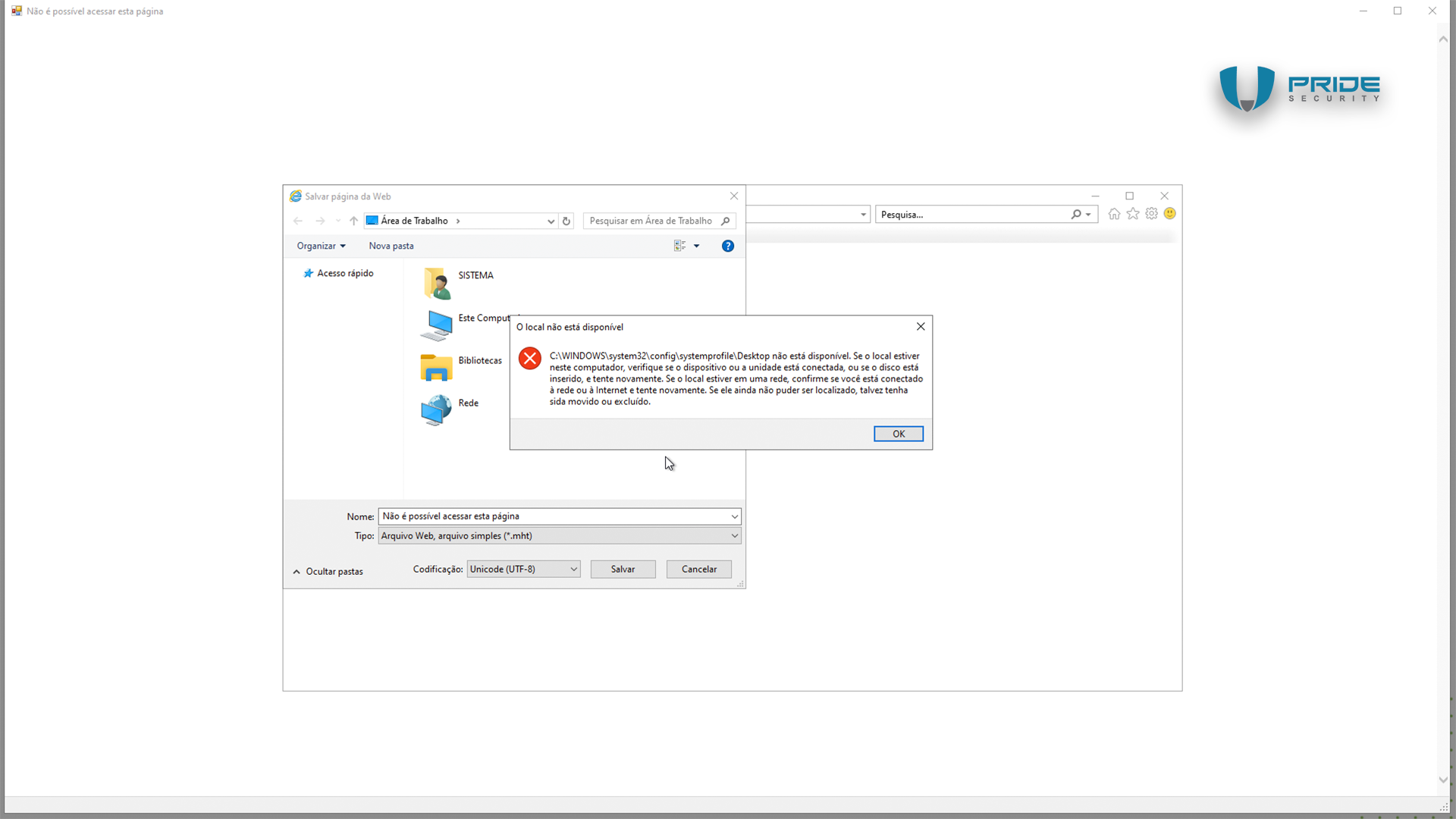
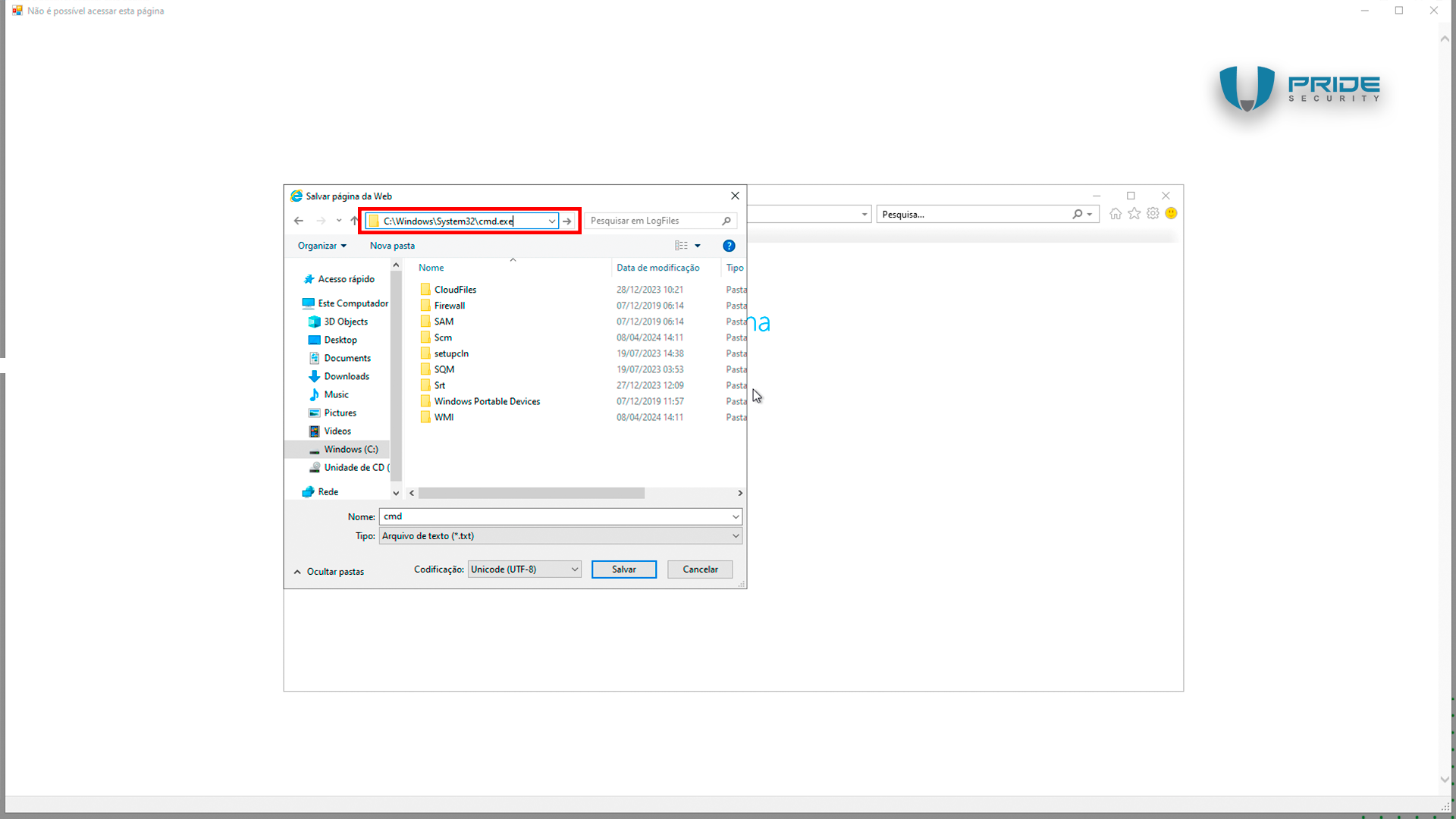
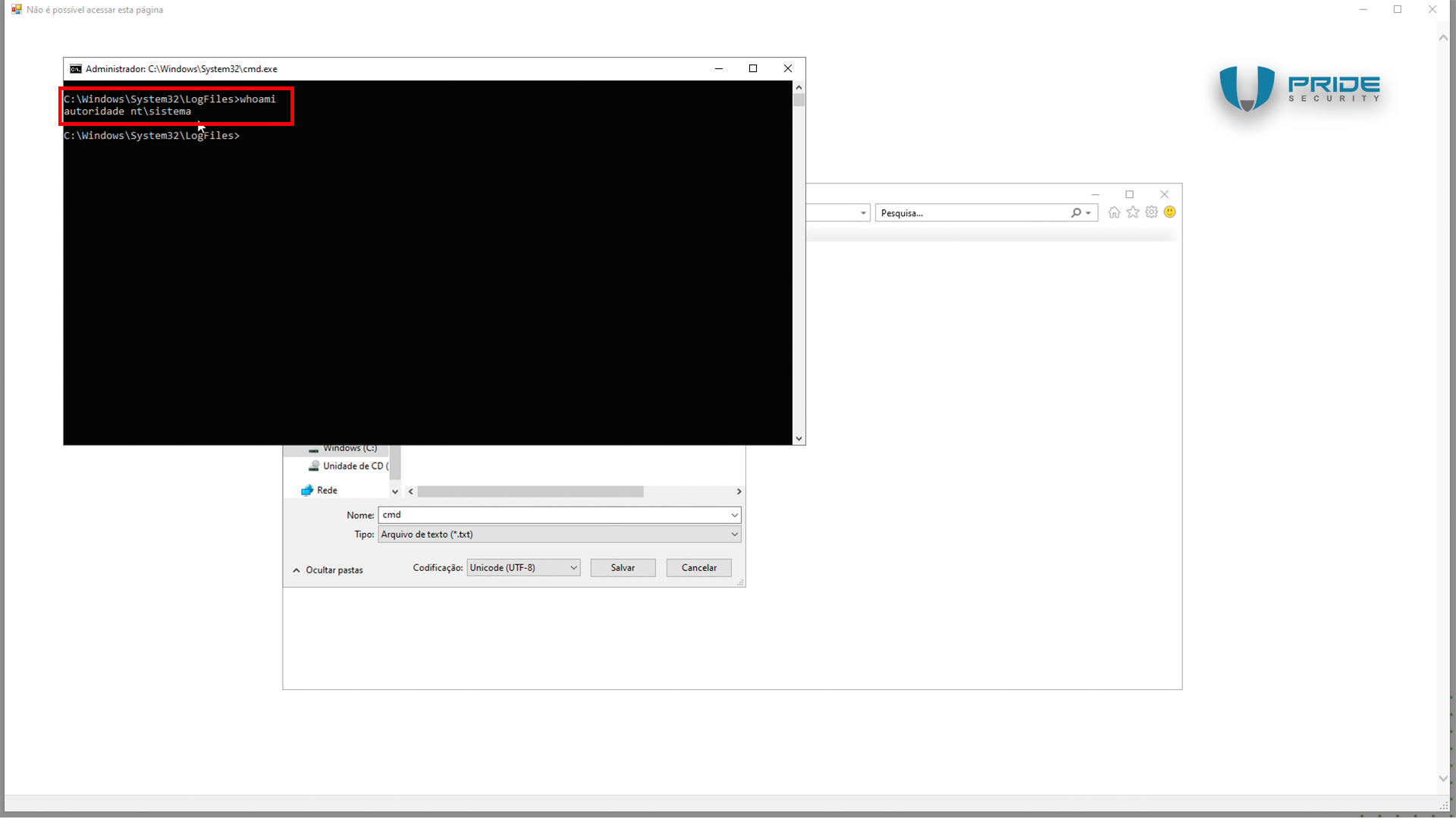
A File Explorer window will appear, displaying the C:\Windows\System32 folder. In the address bar of the save dialog, the attacker simply needs to enter the full path to CMD (C:\Windows\System32\cmd.exe) and execute the command prompt.
When the command prompt (CMD) is open, enter the command 'whoami' to display the privilege level, which will show as NT AUTHORITY\SYSTEM.
Clarifying note
Under specific circumstances, it is possible to execute this attack remotely, as long as the attacker is able to disrupt access to the Horacius server.
From the physical penetration testing to the LPE
As mentioned at the beginning of this blog post, the unauthenticated privilege escalation vulnerability was identified during a physical penetration test. In principle, this blog post could conclude at this point, since the vulnerability has already been detailed and is now documented as CVE-2024-29417. However, it is common for clients to have questions about this type of test. Therefore, we will address some real examples of attacks carried out by PRIDE Security.
During the physical penetration test conducted by PRIDE Security, the team adhered to the standard procedure typical of most physical security assessments, beginning with an observation phase. The morning routine uncovered a pattern: as employees arrived at work, they swiped their badges through the turnstiles, which opened to grant them access to restricted areas. Similarly, visitors authenticated themselves using QR code access ticket. What caught our attention was the behavior observed around lunchtime, when numerous employees and visitors left the premises. Instead of discarding their QR code access ticket as expected, they chose to fold them and tuck them into their pockets. This captured our attention as it is not typical behavior. We will continue to observe and monitor the situation
Upon returning from lunch, it was observed that the visitors pulled crumpled pieces of paper from their pockets. As they approached the security guard, they opened their QR code tickets and passed them through the turnstile, thus ensuring access to the company.
"What drew our attention to this particular scenario?"
Because this isn't a common practice in terms of security.The common procedure is that, after the meal break, that is, after entering and leaving, the visitors must return to reception, reaffirm their identification and obtain a new QR code access ticket for visitors.
This entry allowed visitors to reuse the same crumpled QR code tickets to regain access after lunch, enabling multiple entries and exits on the same day without the need for a new registration. The first measure adopted was to search for a nearby trash can. We soon found one. We started rummaging through this trash can and found some QR code ticket.

Among them, we found some variety of conditions: some were dirtier, crumpled or torn. However, we managed to find one QR code access ticket in acceptable condition, as we can see in this case.

We straightened out the ticket, was reused by the consultant from PRIDE Security. We greeted the security guard, passed this ticket through the turnstile, the turnstile opened, allowing access to the restricted area. Then, the elevator was used to reach the restricted areas, including being able to use a technique known as tailgating.
Tailgating: the technique
Tailgating is simply the act of closely following someone. In other words, it's the act of slipping through a secure entrance in someone else's wake, bypassing security measures. Let's delve into an example. Imagine there is a door equipped with a biometric access control system. An authorized person arrives in front of this door, places their finger on the digital recognition, unlocks the door, opens it, and passes. When the door is closing, the attacker comes very close, holds the door before it closes, and slips through behind them. This is tailgating
Let's examine another real-life scenario, one that we employed in an attack. Here, we approach the entrance of a company. An employee is using their badge to access the restricted location. We positioned ourselves very close to him; as the employee began to pass through the turnstile, we moved in sync as though we were one single person. Once inside, the consultant can move to other areas, using elevators and other passages.
Figure 11 - Tailgating
This type of attack works in a variety of environments. However, there are some turnstiles that sound a beep or alarm when two people attempt to pass through simultaneously. This alert draws the attention of the security guard, inhibiting this attack.
Figure 12 - Access to restricted area
Conclusion
We have reached the end of this blog post, highlighting the identification of the CVE-2024-29417 security vulnerability in the Horacius Identity and Access Management (IAM) system, developed by the company E-TRUST. The vulnerability was independently discovered by Gilson Camelo from PRIDE Security and Wendel G. Henrique during separate penetration testing engagements. If your organization utilizes Horacius, we recommend contacting E-TRUST to obtain more information about addressing this vulnerability.
For those interested in delving deeper into physical penetration testing and curious about turnstiles, I invite you to explore our other posts on the topic: 'Turnstiles from a hacker perspective - Part 1 and Part 2'.
The journey through security continues! Stay tuned!
Acknowledgements
| Name |
|---|
| Felipe Sanches |
| Gilson Camelo |
| Gustavo A. Régis |
| Wendel G. Henrique |
About PRIDE Security
PRIDE Security is a company specialized in information security that focuses on technical excellence and personalized services. Founded by information security experts, we have worked in various types of projects, from ATM (automated teller machines) penetration testing to national security projects.
Composed of an experienced team of more than 15 years in the market and with technical excellence proven by national and international technical recognition, PRIDE Security sees in each project a new challenge to deliver more than expected.
As proof of international technical recognition, our professionals are constantly approved or invited to lecture on security events around the world. We cite below some examples of congresses, conferences and seminars focused on information security, which we participate as lecturers or coordinators of the technical groups:
- Blackhat – USA
- RSA Conference – USA
- Defcon – USA
- ToorCon – USA
- Blackhat – Europe edition
- OWASP AppSec Research – Europe edition
- OWASP AppSecEU09 – Europe edition
- Troppers – Germany
- H2HC (Hackers 2 Hackers Conference) – Brazil
- YSTS (You Sh0t The Sheriff) – Brazil
In addition to lecturing at major security events around the world, our team of experts are also responsible for writing various papers, co-author of offensive technology patent registered in the United States of America (US8756697), finding and publishing security vulnerabilities in famous software such as Sun Solaris, FreeBSD / NetBSD kernel, QNX RTOS, Microsoft ISA Server, Microsoft Word, Adobe Flash, Adobe PDF, among others.
Many organizations of all sizes concerned with information security rely on PRIDE Security. If you desire, we will be pleased to connect you with our customers to share about their experience with our services.